IT vs OT Cyber Security Differences
- Andrew Sario

- Dec 20, 2019
- 5 min read
Updated: Sep 1, 2021
The term Cyber Security is very well known and we have seen the increase in its usage over the years. Taking some data from Google Trends on the search term "cyber security" since 2010 we can see a steady increase over time.
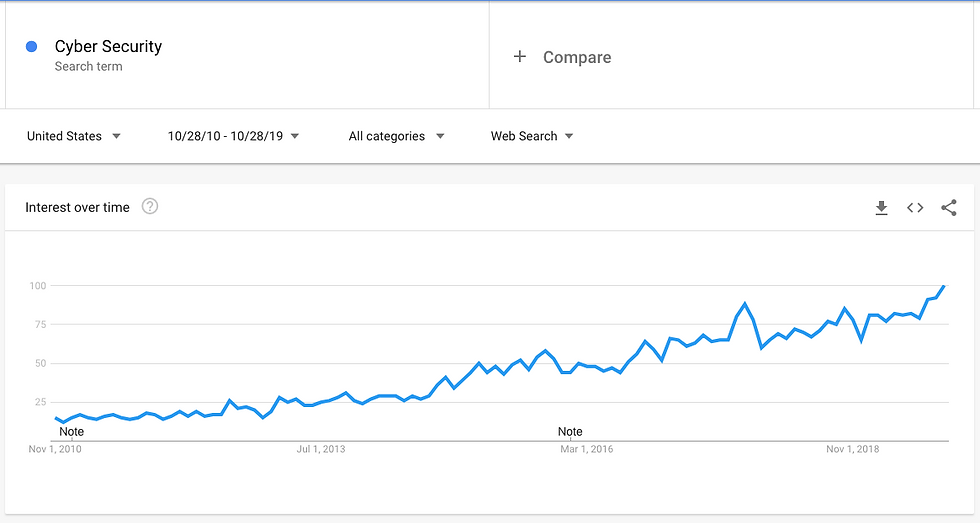
At first glance, this seems to make sense:
Over time as the usage of the internet increases, then hacks and cybercrime increases, so does the concept of Cyber Security.
But there's something missing in this picture. 2 Interesting pieces in so far as google trends search terms are interesting.
When you compare it with the term "hacker" it has been a big trend since 2010 and it's only now that Cyber Security is catching up. So, for a long time hackers have always been a thing but Cyber Security not as much.
Then I thought, maybe the increase is then due to major cyber attacks on critical infrastructure and things of this nature. Comparing this search term shows it hasn't really gained any traction.
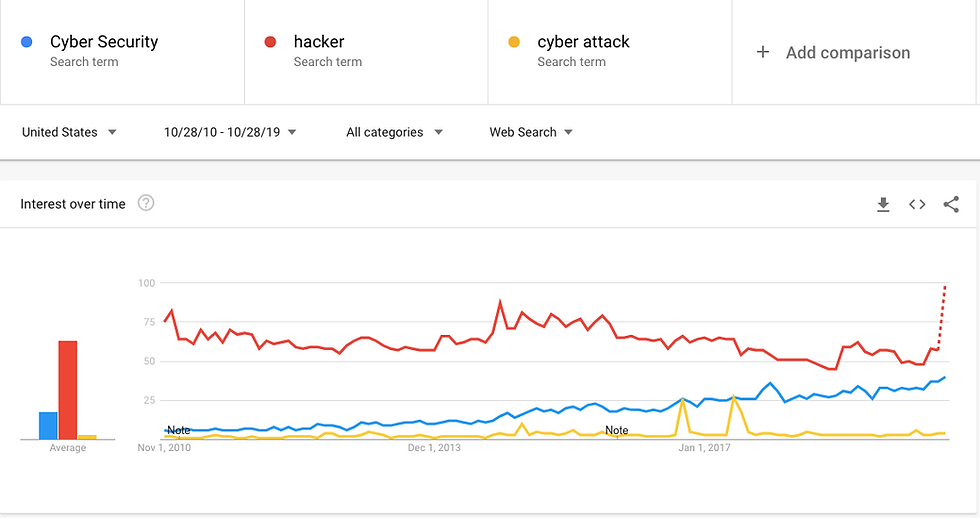
Nonetheless, the simplistic way to look at it is as technology and hyperconnectivity improves, so does the ability for remote attacks to take place. -And they have. 4 billion stolen records in the last decade is no small thing, there's a big focus on data breaches here but there have been significant attacks on OT systems where large processes were impacted. Take sometime to look at Stuxnet the worlds first digital weapon and the Saudi Aramco hack and you get an idea of the types of cyber attacks that happen in industry and their impact.
The target is different.
And so, the security solutions must be different.
IT and OT have common technology, but different goals.
For example here's my IT/OT Car Analogy.
Because the goals have changed therefore the problems you solve are different and so the design changes.
The definition of what is considered good or bad completely changes.
A racing car doesn't care for creature comforts, cup holders. They sacrifice luxuries for the reduction in weight. Whilst a city car doesn't need something that can drink fuel quickly and get them to max speed since likely they will stop more often, be in the car longer and probably want a music player.
Now back to IT vs OT.
IT cares most about Information (lo and behold, it's in the name) whilst OT cares about the process and the operation of that process (wow, also in the name). What does this mean?
An IT system will prioritize protecting data over most things. If a system needs to be restarted so it gets its updates and has less risk of losing data, then so be it.
An OT system will prioritize running the process over most things. If data is lost or not saved or not logged or backed up or updated, sure, as long as the system does not stop running.
This means that the Cyber Security shoe isn't a one size fits all. So let's deep dive now into what are the differences in cyber security solutions. Well, let me first categorize cyber security solutions to form the basis of what it is that we are going to compare. Just to note the 8 Categories listed below aren't from any particular standard, rather a summary or roll up of different standards and known solutions that at a high level can be somewhat put in these headers for simplicity. (This is why there's an entire industry for this beast).
1. Governance
These are document type solutions, the policies and procedures that lift your cyber security. It could include assessments and compliance, etc.
2. Updates
This refers to all firmware, operating systems, software versions that manufacturers or vendors may release to patch issues in previous versions.
3. Hardening and Change Management
This refers to all the configurations that can be made on a system or software to make it more secure. In addition the ability to know what changes are made to the systems.
4. Identification, Authentication and Privileges
Everything to do with knowing who is connecting to the system, how we know who it is and what the identified person is or isn't allowed to do.
5. Monitoring and Reporting
The tools and information necessary to understand what is happening in a system and its networks, typically live and capabilities to report on different metrics and logs.
6. Isolation and Zones
This refers to everything from system and network architecture design, tools and technology for isolation (Firewall, Data Diode, Key switches, DMZ, VPN tunnels, etc) and remote access.
7. Data Protection
This refers to backups, test systems, data encryption (for transmission and for storage), privacy and redundancy.
8. Malware Prevention Systems and Blacklisting/Whitelisting
These are software and hardware solutions that address malware prevention and by extension, unwanted software running. Think Antivirus.
Great! Now we have a list of categories of cyber security solutions that could be in place for any given network or system. The fun part begins where we can now deep dive into some of the major differences (and similarities) of the same solutions in the 2 different environments IT and OT.
In a nutshell
Going through this list you can start to see that across the broad cyber security categories whilst there is a place for both there is a nuance in what guides the implementation.
In short, you find a preference for being informed of issues but no automatic actions taken by the security system whilst in OT environments where in IT environments its about them acting as quickly as possible. Even at the cost of stopping the show, the preference is to protect the data.
This is precisely why you need a specific understanding of OT environments before applying cyber security solutions that are implemented with an IT lens.
Consider both systems can be mission-critical but in most cases OT systems are also safety-critical and so the processes that they run need to be sure they run, 24/7 particularly the safety systems. Operators need access to their systems to maintain their course and ensure no harm to people, environment, process.
Wait a minute, so why now? Why is Cyber Security becoming a rising area for operational technology environments, specifically? From what we have read so far we know that it is trending as a standalone term but why does industry care all of a sudden in 2020? Find out here and make sure you have a full understanding of the topic.
With some effort and practice you will start to see the common patterns emerge and if you break your limiting mindset that they are both technology and therefore the solutions are the same you will become a better OT Cyber Security Engineer.
There are courses and certifications that can help you in this journey such as the CISSP certification and if you're interested to see a tier-list of different certifications that can help you drop a comment.
If you're looking for specific advice or solutions just contact us and leave your question I might be able to help you out.




Comments